Improve Security Posture
By identifying and addressing vulnerabilities, pen testing can help to improve the overall security posture of an organization.
24/7/365 Monitoring & Alerting
Compromise Assessments
Threat Hunting
Vulnerability Management
CMMC Preparation & Assessment
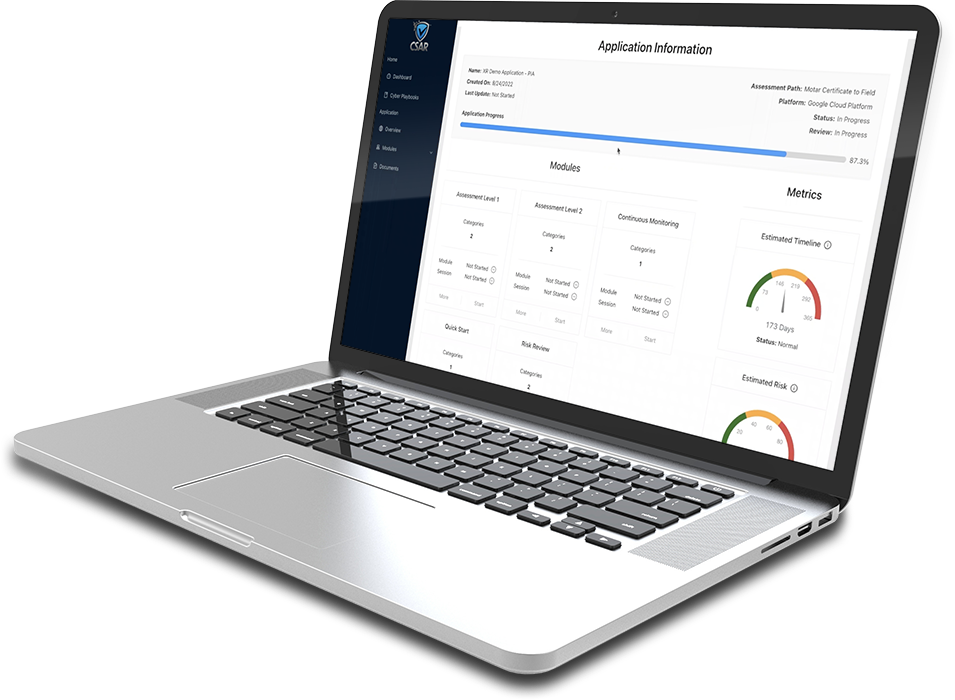
Cybersecurity Assurance Readiness (CSAR/RMF Pro)
ATO/RMF Support
If you are concerned about a potential threat or are experiencing a breach, contact our 24/7/365 emergency hotline at 888-860-0452.
 Subscribe to NetSec News
Subscribe to NetSec NewsSign up to receive our biweekly newsletter that covers what's happening in cybersecurity including news, trends, and thought leadership.
At our core, Ingalls is a company that strives to be helpful to our clients while continuously innovating and evolving our technology and solutions. Since 2010, we have been dedicated to building a team and product that can stay steps ahead of threats, attacks, and vulnerabilities in an ever-changing landscape.
Ingalls Information Security performs penetration testing and vulnerability assessments in order to provide tailored recommendations and reports to help you defend your infrastructure against hackers, cybersecurity attacks, and other malicious threat actors.

Penetration testing is the practice of actively simulating an attack on systems to identify vulnerabilities that an attacker could exploit. By performing regular penetration testing, an organization can proactively identify and address potential vulnerabilities before they can be exploited by malicious actors.

Web application penetration testing is the practice of testing a web application to identify vulnerabilities that an attacker could exploit. The goal of a WAPT is to identify vulnerabilities in an application and provide recommendations for improving its security.

Internal penetration testing is the practice of testing a computer system, network, or web application from within an organization's internal network. The goal of an IPT is to identify vulnerabilities that an attacker could exploit if they were able to gain access to an organization's internal network.

External penetration testing is the practice of testing systems from outside an organization's network, simulating an attack from the internet. The goal of an EPT is to identify vulnerabilities that an attacker could exploit if they were able to gain access to an organization's external-facing systems and infrastructure.
A vulnerability assessment is the process of identifying and evaluating vulnerabilities in a computer system, network, or web application. The goal of a vulnerability assessment is to identify vulnerabilities that could be exploited by an attacker, and to provide recommendations for improving the system's security. A vulnerability assessment is typically less comprehensive than a penetration test, as it does not involve actively attempting to exploit vulnerabilities. Instead, it relies on tools and techniques to identify vulnerabilities and assess their potential impact.
By identifying and addressing vulnerabilities, pen testing can help to improve the overall security posture of an organization.
Pen testing can help to validate the effectiveness of security measures and identify any gaps or weaknesses.
Pen testing can provide a better understanding of the potential impact of a successful attack on systems, which can help you to prioritize remediation efforts.
In some cases, pen testing may be required to meet regulatory or compliance requirements.
Our Professional Services team has expert consultants who specialize in developing integrated cybersecurity risk management services that can be customized for any business or organization. Download the PDF brochure to learn more.
Sign up to receive our biweekly newsletter that covers what's happening in cybersecurity including news, trends, and thought leadership.
