2 min read
Ingalls Spring 2024 Intern Review: Cierra Moret
In this Intern Review, we hear from Cierra Moret about what it's like working at Ingalls and what's next in her cybersecurity career journey.
Read More24/7/365 Monitoring & Alerting
Compromise Assessments
Threat Hunting
Vulnerability Management
CMMC Preparation & Assessment
Cybersecurity Assurance Readiness (CSAR/RMF Pro)
ATO/RMF Support
If you are concerned about a potential threat or are experiencing a breach, contact our 24/7/365 emergency hotline at 888-860-0452.
 Subscribe to NetSec News
Subscribe to NetSec NewsSign up to receive our biweekly newsletter that covers what's happening in cybersecurity including news, trends, and thought leadership.
At our core, Ingalls is a company that strives to be helpful to our clients while continuously innovating and evolving our technology and solutions. Since 2010, we have been dedicated to building a team and product that can stay steps ahead of threats, attacks, and vulnerabilities in an ever-changing landscape.


2 min read
In this Intern Review, we hear from Cierra Moret about what it's like working at Ingalls and what's next in her cybersecurity career journey.
Read More
2 min read
In this Intern Review, we hear from Jansen Mitchell about what it's like working at Ingalls and what's next in his cybersecurity career journey.
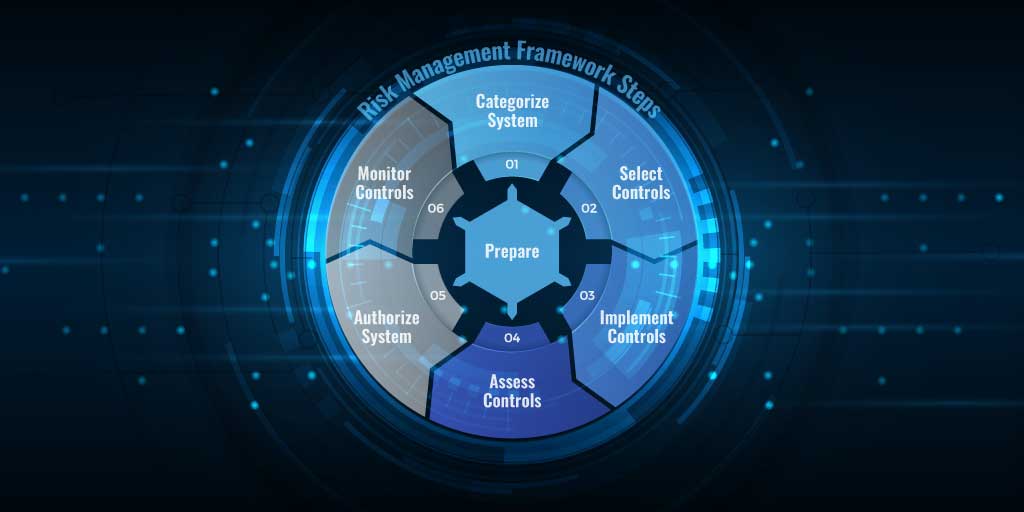
2 min read
The phrase "time is of the essence" has never been more critical than now with our geopolitical adversaries, particularly China, not only gaining...

2 min read
In this Intern Review, we hear from Prashanth Kodiyalam about what it's like working at Ingalls and what's next in his cybersecurity career journey.

2 min read
In this Intern Review, we hear from Nathaniel Funderburk about what it's like working at Ingalls and what's next in his cybersecurity career journey.

17 min read
Meet Ingalls Information Security Interns! We thank each of them for all their hard work and dedication. Our interns represent an incredible...

2 min read
In today's digital landscape, the importance of cybersecurity cannot be overstated. As businesses increasingly rely on technology to streamline...
Sign up to receive our biweekly newsletter that covers what's happening in cybersecurity including news, trends, and thought leadership.
